Actualiser README.md
This commit is contained in:
21
README.md
21
README.md
@@ -0,0 +1,21 @@
|
||||
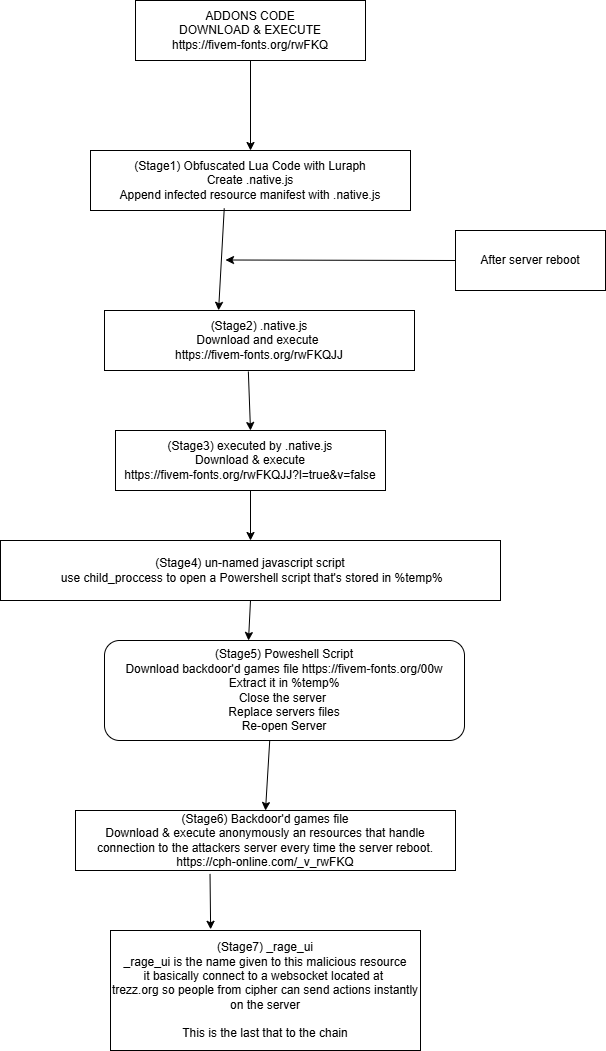
# FIVEM CIPHER PANEL BASIC ANALYSIS AND INFECTION PAYLAOD DUMPS
|
||||
|
||||
|
||||
** In this repo you will find **
|
||||
-> Infection Dumps from 15/03/2025
|
||||
-> A schema on how it work
|
||||
-> The repo doesn't contain de-obfuscated payloads.
|
||||
|
||||
-> About Payoad obfuscation
|
||||
-> Stage 1 : Use Luraph
|
||||
-> Stage 2 : use some basic custom Xor encryption really easy to decrypt even chatgpt do it.
|
||||
-> Stage 3 : Use https://obfuscator.io/ you can partially revert with https://obf-io.deobfuscate.io/ (You will have to cleanup junk code manually.)
|
||||
-> Stage 4 : Some VM Like obfuscation for Javascript didn't look into it.
|
||||
-> Stage 5 : Not obfusctated clear-text powershell.
|
||||
-> Stage 6 : Backdoor'd DLLs and stuff didn't take the time to reverse it.
|
||||
-> Stage 7 : For lua files its Luraph, For JS files its https://obfuscator.io/
|
||||
|
||||
|
||||
# A schema on how it works.
|
||||
|
||||
|
||||
Reference in New Issue
Block a user